Connect Data Connection Manager (DCM) to your HashiCorp instance, so that later you can fetch authentication data from HashiCorp to your workflow.
Go to File > Manage Connections to open DCM.
Select External Vaults in the bottom-left corner.
Select the + New button to add a new Vault to DCM.
Choose your HashiCorp Vault technology. Only the KV secrets engine is supported, in versions 1 and 2.
Enter a custom name for this Vault connection.
Next, enter the URL and Namespace, where your HashiCorp Vault is located, and select Save.
For example URL:
https://vault.your-company.hashicorp.cloud:8200Namespace:
Namespace1Select + Connect Credential and choose Create New Credential in the Credential dropdown.
Fill in the fields based on your selected authentication method to access HashiCorp (username and password for basic authentication or when using LDAP, ClientId, Secret for OIDC, or mTLS Certificate).
Select Create and Link.
Now, you can select this newly created Vault when you create new Credentials.
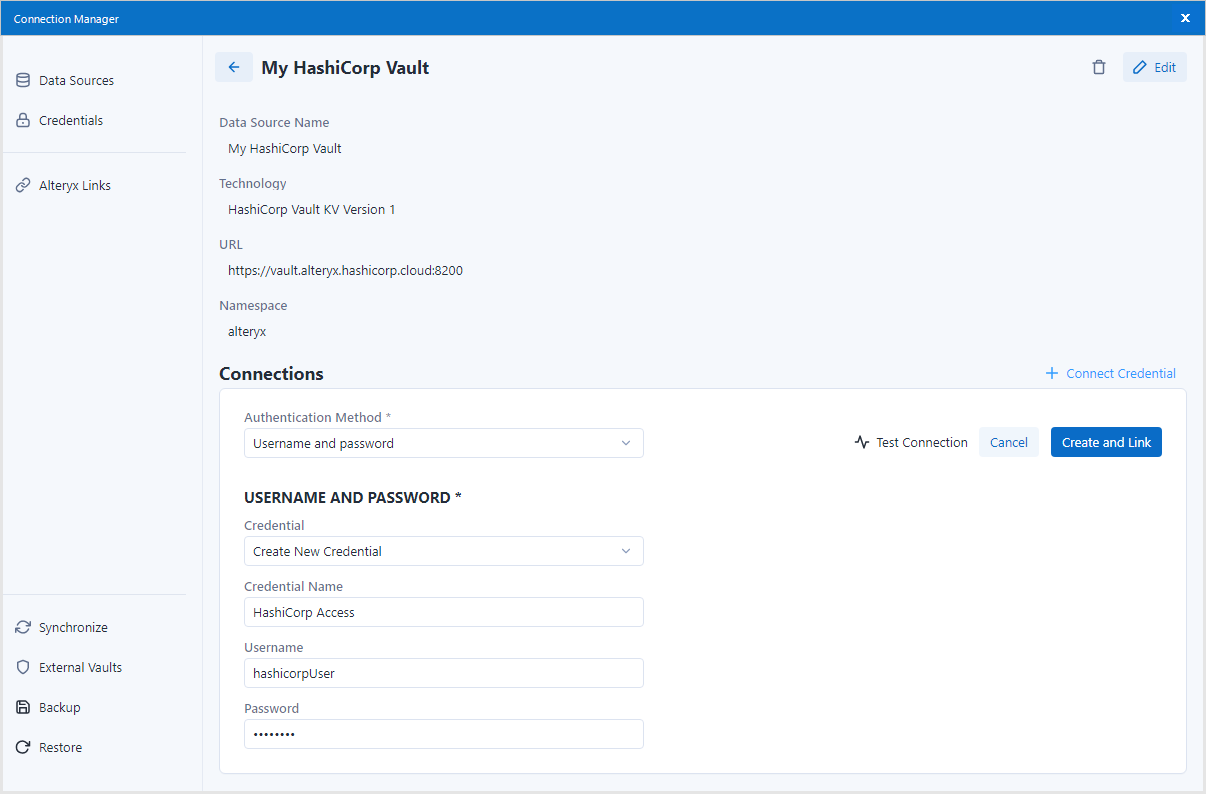
To configure the mTLS certificate credential for HashiCorp Vault, you need to fill in the following information:
Credential Name: Choose a custom name for referencing the created credential.
SSL Certificate: Specify the file path to the certificate file with the supported types mentioned below.
Certificate Type: Choose from auto, DER, P12, or PEM. Leave it on auto to automatically determine the certificate type based on the file extension.
Key: If the SSL Certificate does not contain the key file, provide the file path to the key itself. The only supported file type is .key.
Password: Enter the password for the key (or certificate if a single file) if the file is protected.
HashiCorp Vault Certificate Role: Optionally, specify the desired role for authentication using the certificate, following the certificate roles configuration in your HashiCorp Vault.
For self-signed certificates, you must add the certificate authority as a trusted root certificate authority to access the Vault using a TLS certificate. To create credentials for fetching secrets from the Vault, follow the same process as with any other available form of authentication.
Create a new DCM Credential, which will use the External Vault connection to get authentication data from HashiCorp.
Go to File > Manage Connections to open DCM.
Select Credentials in the top-left corner.
Select the + Add Credential button to add a new Credential.
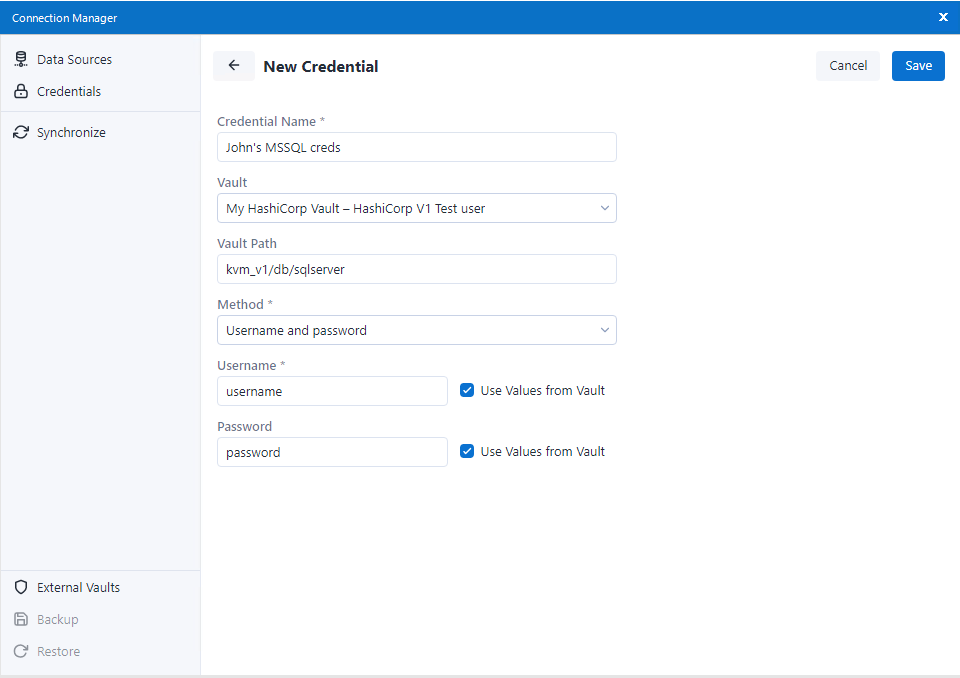
Enter a name for your new Credential.
In the Vault dropdown, choose the HashiCorp instance you previously created.
Fill in the Vault Path field with the path to the authentication data in your HashiCorp Vault.
For example, you have a username and password for your Microsoft SQL database saved in HashiCorp, the path could be this: "vault_name/databases/mssql".
To read the secret values from the Vault, the HCV HTTP API is used, hence the requests are constructed differently, but the Vault Path entered into DCM remains the same for both versions 1 and 2 of the KV secrets engine.
For KV version 1, the request URL is constructed as [vaultUrl]/v1/secret/[vaultPath], e.g. to https://my-vault.hashicorp.cloud/v1/secret/vault_name/database/mssql.
For KV version 2, the request URL is constructed as [vaultUrl]/v1/secret/data/[vaultPath], e.g. to https://my-vault.hashicorp.cloud/v1/secret/data/vault_name/database/mssql.
Next, choose your preferred Method of authentication. This method should match the authentication data you want to fetch from HashiCorp.
For example, if I want to get the Username and Password from HashiCorp, I will select the "Username and password" option.
Make sure the Use Values from Vault check box is enabled, if you want the authentication data to be fetched from HashiCorp. Then, each corresponding field should contain the key, under which is the value saved in your HashiCorp.
For example, if my Username is saved in HashiCorp under a key named "SQLUsername1", then I will check "Use Values from Vault" and enter "SQLUsername1" in the Username field.
Select Save.
Now, you can use this newly created Credential for a corresponding Data Source when you configure a workflow tool.
You can use your new Credential in a workflow. This flow is identical to using a Credential stored in DCM.
To start create a new Workflow, and add some Input or Output Data tools.
For example, I can add the Input Data tool.
Make sure the tool is configured to use DCM (enable the Use Data Connection Manager (DCM) check box in my Input Data tool).
Set up your connection, and choose your desired technology.
For example, I will select "MSSQL Server Quick Connect" in my Input Data tool.
Once the Connection Manager window opens, choose an existing Data Source or create a new one.
Select + Connect Credential and choose the previously created credential (the one that gets authentication data from HashiCorp).
For example, I will select the Credential that I named "John's MSSQL creds".
Select Create and Link.
Select Connect.
Now, the connection is set up. You can proceed to configure any specific details related to your data source technology (for example, select database table, record limit, etc.).
Once your workflow is ready, run it to see if you correctly authenticate to your Data Source using Credentials obtained from your HashiCorp Vault.