In this chapter, you will connect DCM to your AWS Secrets Manager instance, so that later you can fetch authentication data from AWS Secrets Manager to your workflow.
Go to File > Manage Connections to open DCM.
Select External Vaults in the lower-left corner.
Select the + New button to add a new Vault to DCM.
Select the AWS Secrets Manager technology.
Enter a custom name for your Vault connection.
Next, enter the endpoint pointing to your AWS Secrets Manager in the format of
{protocol}://{servicename}.{region}.{domain}and select Save.Example:
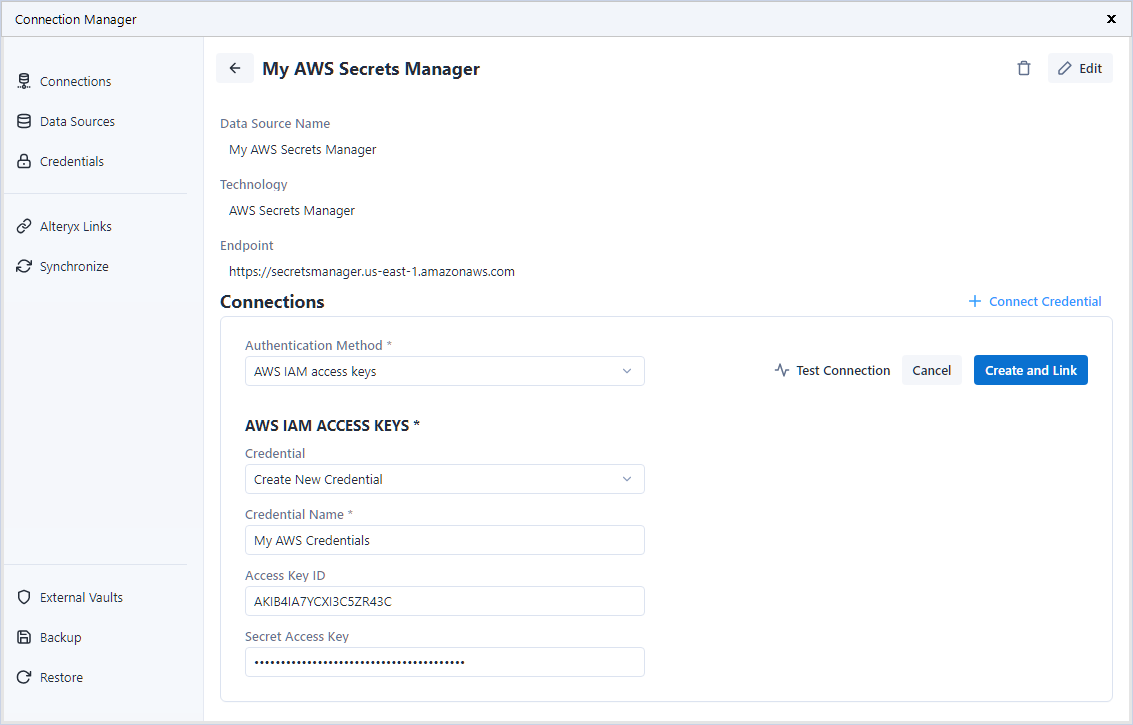
https://secretsmanager.us-east-1.amazonaws.comSelect + Connect Credential and then select Create New Credential in the Credential dropdown.
Enter your AWS IAM access keys required to access AWS Secrets Manager.
Select Create and Link.
From now on, you will be able to select this new Vault when you create new Credentials.
In this chapter, you will create a new DCM Credential, which will use the External Vault connection from the previous chapter to get authentication data from AWS Secrets Manager.
Go to File > Manage Connections to open DCM.
Select Credentials in the upper-left corner.
Select the + Add Credential button to add a new Credential.
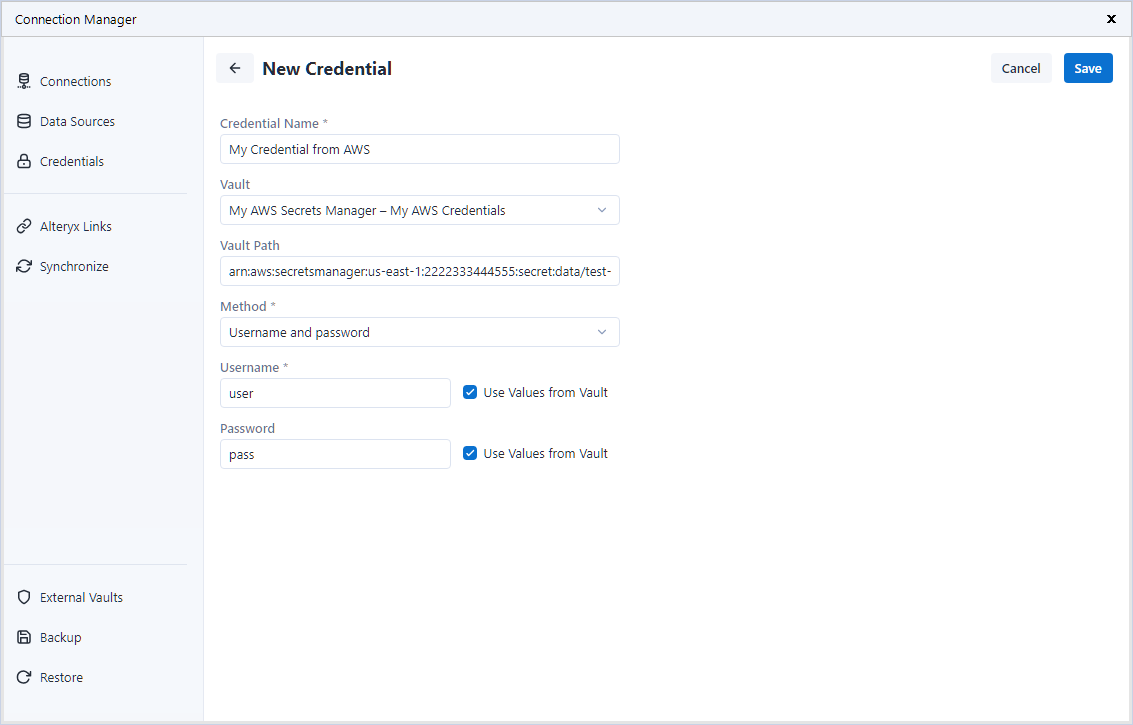
Enter a name for your new Credential.
In the Vault dropdown, select the AWS Secrets Manager instance you created in the previous chapter.
In the Vault Path field, enter the secret name or ARN of the secret from your AWS Secrets Manager.
For example, if you have a username and password for my Microsoft SQL database saved in AWS Secrets Manager, the ARN could be: arn:aws:secretsmanager:us-east-1:222334445566:secret:data/test-AAbbCC and the secret name in such case is data/test.
Next, select your preferred Method of authentication. This method should match the authentication data you want to fetch from AWS Secrets Manager.
For example, if you want to get the Username and Password from AWS Secrets Manager, select the Username and password option.
Make sure the Use Values from Vault checkbox is selected if you want to fetch the authentication data from AWS Secrets Manager. Then, enter the key values from your AWS Secrets Manager in each corresponding field.
For example, if your Username is saved in AWS Secrets Manager under a key named SQLUsername1, check Use Values from Vault and enter SQLUsername1 in the Username field.
Select Save.
From now on, you’ll be able to use this new Credential for a corresponding Data Source when you configure a workflow tool.
In this chapter, you will use your new Credential from the previous chapter in a workflow. This flow is identical to using a Credential stored in DCM.
Create a new Workflow and add input or output data tools.
For example, add the Input Data tool.
Make sure the tool is configured to use DCM by enabling the Use Data Connection Manager (DCM) checkbox in my Input Data tool.
To set up your connection, select your preferred technology.
For example, select MSSQL Server Quick Connect in the Input Data tool.
When the Connection Manager window opens, select an existing Data Source or create a new one.
Select + Connect Credential and choose the credential created in the previous chapter the one that gets authentication data from AWS Secrets Manager.
For example, select the Credential that we named My Credential from AWS.
Select Create and Link.
Select Connect.
Now, the connection is set up. You can proceed to configure any specific details related to your data source technology like selecting a database table or record limit.
Once your workflow is ready, run it to test if it correctly authenticates to your Data Source using Credentials obtained from your AWS Secrets Manager.